
INTRODUCTION:
It’s always been known that many perils exist on the internet. Many have been the victim of stolen personal information like passwords and many have lost money to schemes like the Nigerian scam. Just when you think you have secured your life, someone comes along and shatters your confidence because of evil operators attacking financial institutions that put your information at risk. North Korean organizations in association with the North Korean government have ongoing efforts to hack the DeFi community. Ionut Ilascu, a cybersecurity technology writer, provides us with some insight into the DPRK network in his article below.
_____________________________________________________________________
Hackers associated with the North Korean government have been distributing a trojanized version of the DeFi Wallet for storing cryptocurrency assets to gain access to the systems of cryptocurrency users and investors.
The threat actor relied in this attack on web servers located in South Korea to push the malware and to communicate with the installed implants.
Fully functional backdoor
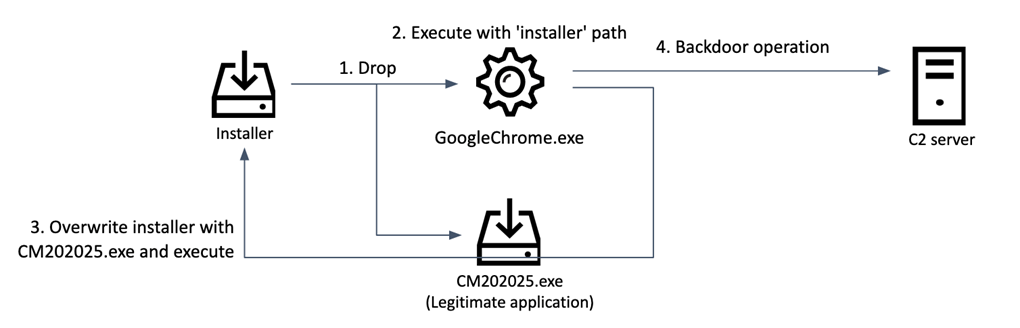
Researchers at cybersecurity company Kaspersky discovered recently a malicious variant of the DeFi Wallet app, which installed the legitimate application along with a backdoor disguised as the executable for the Google Chrome web browser.
The trojanized DeFi application came with a compilation date from November 2021 and added a full-featured backdoor when executed on the system.
It is unclear what distribution method the hackers used but phishing emails or contacting victims over social media are plausible scenarios.
According to the researchers, the malware planted this way has “sufficient capabilities to control” the victim host by executing Windows commands, deleting files, launching or terminating processes, enumerating files along with associated metadata, or connecting the computer to a given IP address.
Additional functions allow the malware operator to collect information about the system (IP, name, OS, CPU architecture) and the drives (type, free space available), download files from the command and control server (C2), and get a list of files stored in a specific location.
DPRK connections
Kaspersky researchers worked with the South Korea CERT (Computer Emergency Response Team) to take down some of the domains used in this campaign and could analyze and compare the C2 scripts.
The findings revealed overlaps with other operations from attackers linked to North Korea, generically referred to as the Lazarus group.
“We believe with high confidence that the Lazarus group is linked to this malware as we identified similar malware in the CookieTime [malware] cluster,” Kaspersky
The CookieTime malware cluster is also known as LCPDot by Japan CERT and has been connected with the DPRK operation Dream Job, which lured victims with fake job offers from prominent companies.
Recent activity related to Dream Job was exposed earlier this month by Google’s Threat Analysis Group (TAG), which found that North Korean threat actors had used an exploit for a zero-day, remote code execution bug in Chrome to target individuals working for news media, IT companies, cryptocurrency, and fintech organizations.
Furthermore, Kaspersky notes “that the CookieTime cluster has ties with the Manuscrypt and ThreatNeedle clusters, which are also attributed to the Lazarus group.”
The connections between the current trojanized DeFiWallet app and other malware attributed to North Korean hackers extend not only to the malware code but also to the C2 scripts, which share many functions and variable names.
North Korean threat groups
It is worth noting that Lazarus is the generic term used for all threat activity from state-sponsored North Korean actors. However, there are multiple threat groups within the DPRK, each working under different institutions/departments of the country’s intelligence apparatus.
Using data collected over 16 months from its cyber activity tracking for the entire country, OSINT monitoring, defector reporting, and imagery analysis, Mandiant researchers created an assessment of DPRK’s structure for its cyber programs.

According to their map, targeting cryptocurrency heists are likely within the scope of financially-motivated groups within the 3rd Bureau (Foreign Intelligence) of the country’s Reconnaissance General Bureau (RGB).
Kaspersky notes that the recently discovered activity is similar to the compromise of the MetaMask DeFi wallet, attributed to another North Korean hacker group they call BlueNoroff.
The researchers published technical details on the backdoor and how it spawned from the trojanized DeFi application and shared indicators of compromise for the malware and the compromised legitimate first-stage C2 servers used for the attack.
Via this site
